
Goodbye, Lstu. Welcome, rs-short!
A free/libre, homemade link shortener written in Rust
Hello,
It has been a few months since we became aware of the amount of spam we were receiving on our link shortener, Lstu.
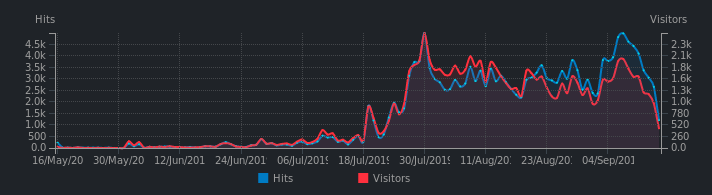
The service opened on 23 May 2019 and remained under the radar for a while…. Until the end of July, when malicious activity began to develop. Links created by bots, redirecting to scamming sites, illegal or pornographic content, have started to invade our database.
Lstu didn’t have a captcha, so we were in a lot of trouble; we didn’t have a solution to this problem.
We had configured fail2ban to ban an IP after a certain number of links created per day. It was effective, but far from being enough: IPs were numerous.
We started cleaning up on 10 September, where we counted 11 767 URLs, 99.5% of which were created by spammers.
Four days later, we found that 1000 additional malicious links had been created since the last cleanup.
We had no choice but to put the instance in “read-only” mode (block the creation of new links) and think quickly about a solution.
🔗Unsuspected consequences
When we first identified the first traces of suspicious activity, we thought it was okay, that users can do whatever they want with their links, that we need to keep the tool neutral about their activity.
But we have gradually thought about the consequences: given the type of links created, there is no doubt that they have been used for spam purposes, especially by email.
We know that major email providers reads the content of emails to determine whether it is spam or not. If spammers sends emails containing a link to our shortener (s.42l.fr), it will probably affect the reputation of our domain name and IP, which would cause major problems for our email service.
As a precaution, we have checked whether our IP/domain name has been included in known blacklists, but this does not seem to be the case.
🔗Other problems
In addition, Lstu was taking a lot of RAM (between 150 and 220 MB, even at rest), which was not acceptable for a service that is supposed to be minimalist.
We have already reported the problem to Framasky (his developer) but according to him, it could be a leak in the Mojolicious framework, used in its design. Let’s not forget that Lstu is written in Perl.
And since we can’t read Perl, we couldn’t modify the service to suit our needs.
🔗Solution?
We searched among the existing solutions, but nothing suited our needs (no captcha, not enough customization, most of the projects were in PHP, in short, nothing very attractive…:D).
We have therefore developed a software in Rust with the same goal, but very light in functionalities (it was written in one week!)
We use the Rocket web framework. The service runs in 1000 lines of code, with, no JS, no CSS framework, no tracking, only the bare minimum.
Its consumption is ridiculous (between 8 and 12 MB of RAM).
It includes a captcha that should deter a good part of the spammers for a while.
Finally, it is of course open for contribution under the Mozilla Public License 2.0, the source code is available here.
See you soon,
~ N&B
English translation by Fabien.